Dubai, United Arab Emirates — Acronis, a global leader in cyber protection, released its latest cyberthreats and trends report for the second half of 2022 which found that phishing and the use of MFA fatigue attacks, an extremely effective method used in high-profile breaches, are on the rise. Conducted by Acronis’ Cyber Protection Operation Center, the report provides an in-depth analysis of the cyberthreat landscape including ransomware threats, phishing, malicious websites, software vulnerabilities and a security forecast for 2023.
Of note, the report found that threats from phishing and malicious emails have increased by 60% and the average data breach cost is expected to reach US$5 million by next year. The research team who authored the report also saw social engineering attacks jump in the last four months, accounting for 3% of all attacks. Leaked or stolen credentials, which allow attackers to easily execute cyberattacks and ransomware campaigns, were the cause of almost half of reported breaches in H1 2022.
“The last few months have proven to be as complex as ever – with new threats constantly emerging and malicious actors continuing to use the same proven playbook for big payouts,” said Candid Wüest, Acronis VP of Cyber Protection Research. “Organizations must prioritize all-encompassing solutions when looking to mitigate phishing and other hacking attempts in the new year. Attackers are evolving, using some of the tools, like MFA, that we rely on to protect our employees and businesses against us.”
Middle East and Africa Cybersecurity Landscape
As the Middle East region continues to grow its digital ecosystem, solid cybersecurity strategies remain a top priority on the back of heightened data breaches. According to security analysts, breaches reported in the Kingdom of Saudi Arabia, for example, could reach an average of US$7 million as the country continues to report one out of five attacks to be ransomware.
With the average cost of ransomware attacks increasing every year, factors such as weak credentials, phishing emails, and unpatched vulnerabilities remain the top cyber-attacking vectors. In the UAE, targeted organizations lost over US$1.4 million in ransomware, forcing over 40% of the impacted companies to shut down. Following this worrying trend, the UAE Cyber Security Council announced the adoption of stringent cybersecurity standards to safeguard the country’s digital space.
Ranked as the sixth-most dense region for cybercrime in the world, cybercrime victims in South Africa surged from 14.1 victims per one million internet users in 2019 to 50.8 victims in 2020. Most recently, the country enacted its cybersecurity act, which clearly defines cybercrimes in a bid to effectively regulate and prosecute them.
In Kenya and Nigeria, financial phishing attempts rose significantly in Q1 and Q2 of 2022 as banks, online payment systems, and e-commerce websites were targeted. In Kenya, over 100,000 financial phishing attacks were detected – a 201% increase compared to Q1 and Nigeria has reported over 61,000 financial phishing attacks, representing an increase of 79% compared to Q1.
Report Highlights: Threat Landscape Sees New Challenges
As security tactics and the technologies associated with them evolve, so do the threat actors trying to break into organizations and their ecosystems. The constant feed of ransomware, phishing and unpatched vulnerabilities demonstrates how crucial it is for businesses to reevaluate their security strategies.
Ransomware Continues to Worsen:
- Ransomware continues to be the number one threat to enterprises and businesses including government, healthcare and organizations in other sectors.
- Each month in the second half of this year, ransomware gangs were adding 200-300 new victims to their combined list.
- The market of ransomware operators was dominated by 4-5 players. By the end of Q3 the total number of compromised targets published for the main operators in 2022 were as follows:
- LockBit - 1157
- Hive - 192
- BlackCat - 177
- Black Basta – 89
- 576 publicly mentioned ransomware compromises in Q3, a slight increase from Q2.
- The number of ransomware incidents decreased slightly in Q3, after a high during the summer months. From July to August, Acronis saw a 49% increase in blocked ransomware attacks globally, followed by a decrease of 12.9% in September and 4.1% in October.
- There is a shift towards more data exfiltration as the main actors are continuing to professionalize their operations. Most of the large players have expanded to MacOS and Linux and are also looking at the cloud environment.
Phishing and Malicious Emails Remain Successful for Threat Actors:
- The most-attacked countries in terms of malware per user in Q3 of 2022 were South Korea, Jordan and China.
- An average of 7.7% of endpoints tried to access some malicious URLs in Q3 2022, slightly reduced from 8.3% in Q2.
- The country with the most clients experiencing malware detections in October 2022 was the United States with 22.1%, followed by Germany with 8.8% and Brazil with 7.8% which are very similar to the Q2 numbers, except for US and Germany which had a small increase, especially in financial trojans.
- Spam rates have increased by over 15% — reaching 30.6% of all inbound traffic.
- Email-borne attacks are targeting virtually all industries. By analyzing the top 50 most attacked organizations, it seems that the most attacked industries are:
- Construction
- Retail
- Real estate
- Professional Services (Services and computers & IT)
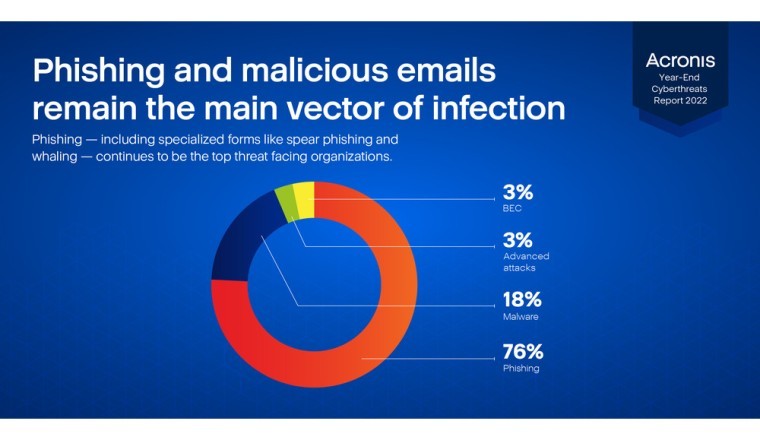
- Finance
- Between July and October 2022, the proportion of phishing attacks has risen by 1.3x reaching 76% of all email attacks (up from 58% in H1 '2022). This rise is at the expense of the proportion of malware attacks.
Unpatched Vulnerabilities Prove Fruitful into the Second Half of the Year:
- Acronis continues to see and warn businesses and home users that new zero-day vulnerabilities and old unpatched ones are the top vector of attack to compromise systems.
- While software vendors try to keep up and release patches regularly, quite often it is still not enough -- a lot of attacks succeed due to unpatched vulnerabilities.
- Microsoft:
- Another phishing campaign targeting Microsoft did impersonate "the Microsoft team" and tried to bait the recipients into adding their memo text onto an online memorial board "in memory of Her Majesty Queen Elizabeth II" when she passed away in September.
- Another large-scale phishing campaign was spotted targeting credentials for Microsoft’s M365 email services. It is aimed at fin-tech, lending, accounting, insurance, and Federal Credit Union organizations in the US, UK, New Zealand, and Australia.



















Facebook Conversations
Disqus Conversations